Due to the awesome awesomeness of the NSA Virtual Nexus recommends that you get and use a PGP key to sign and encrypt your emails. Before you ask what PGP is, let us tell you why you care. SIGNING AND ENCRYPTING YOUR EMAILS MAKES THEM UNREADABLE TO THOSE WITHOUT THE PRIVATE KEY. Now, if you only sign, but do not encrypt, then the emails cannot be changed but can still be read. If you sign and encrypt, they can neither be changed, nor read by those who do not have the private key that decrypts them.
What is PGP?
PGP stand for Pretty Good Privacy. If we ask our friend Jimmy Wales over at Wikipedia, he gives us this answer:
“Pretty Good Privacy (PGP) is a data encryption and decryption computer program that provides cryptographic privacy and authentication for data communication. PGP is often used for signing, encrypting and decrypting texts, e-mails, files, directories and whole disk partitions to increase the security of e-mail communications. It was created by Phil Zimmermann in 1991.”
Since the original PGP was bought by that paragon of Internet perfection, Network Associates, aka NetASS or NAI, the Free Software Foundation build its own Open Source PGP called GnuPGP or “GPG”. Naturally we are all about the open standards, so we recommend this product in this tutorial.
So again what does GPG do?
It enables your private communications to remain private and your public ones to remain unchanged.
Digital Signatures
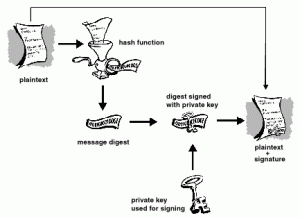
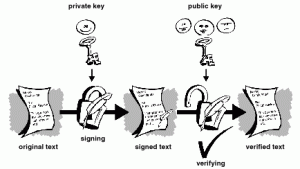
When you sign a message before sending it over the Internet, you send a digitally signed “hash” or mathematical function that shows that your message is exactly the same when received as when you sent it. The process is as follows.
- Write a message to a recipient.
- Hash the binary value of your message.
- Digitally sign the hash value with your private key.
- Recipient receives message, verifies that the hash was signed using your public key.
- Hashes its value.
- Compares your digitally signed hash to the computed hash.
- If hashes are identical your message was unchanged.
Encryption
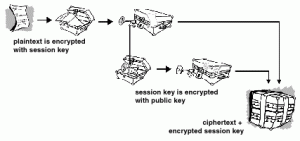
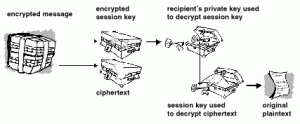
When you encrypt an email you encrypt it with a one-time session key. This key is then encrypted with the recipient’s public key. When the recipient receives the message he or she decrypts the session key with the recipient’s private key. Once the key is available it is used to decrypt the message.
- Compose message.
- Generate session key and encrypt message.
- Encrypt key with recipient public key.
- Send message.
- Recipient receives encrypted message.
- Decrypts session key with recipient private key.
- Decrypt message with session key.
GPG Good
Now after all of the hullaballoo lets see how to implement this. Remember, GnuPGP good, it protects you and your communications from prying eyes or manipulative people. Now GPG works on OSX (Apple), Windows (Microsoft), and Linux (Various). Our since we specialize in Mac’s, this tutorial will show you how to enable GPG on OSX.
Install GPG Tools
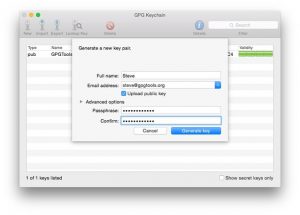
First go to the download link for GPG2 and download and install it on OSX. The instructions are clear on their website so I will not repeat them here.
Once installed you will use your Apple Mail client. Again the instructions are clear on the GPG Tools website. Most importantly, make sure to create your key and protect it upon your system. Backup your key regularly to secure media. You can do this using the GPG Keychain on OSX. Start using your secure email today, or hire Virtual Nexus to teach your firm how.
http://en.wikipedia.org/wiki/Pretty_Good_Privacy#OpenPGP
http://www.pgpi.org/doc/pgpintro/#p1
https://gpgtools.org/#gpgsuite
